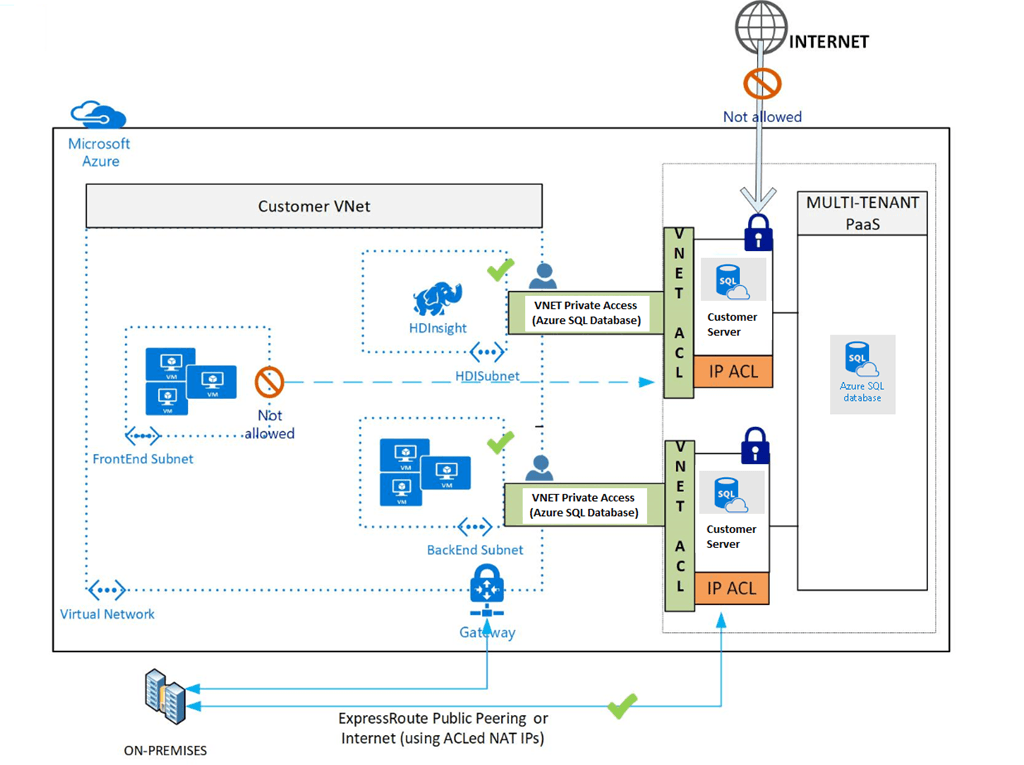
Azure SQL Database and Data Warehouse endpoint services let you isolate the connectivity of your SQLDB and subnets within the VNET. The availability of services is limited only to West Central US, East US1, and West US2 regions. The traffic will remain with the Azure network irrespective of connectivity that is present on Azure SQL Database pubic endpoints. Database admin and network admin can split their roles by using the provision of VNET Service Endpoint. It creates a new entity and supports the RBAC roles.
What are the Limitations of Data Warehouse VNET Service Endpoints Public Preview?
The limitations are as following:
- 128 Virtual Network Based ACLs for each SQL Server.
- Applicable only to ARM VNETs.
Important Consideration
The user needs to open the Network Security Groups to enable Azure SQL Database traffic. To attain PaaS services, you should open only IP ranges. The public IP addresses automatically switch to VNET private IP addresses when VNET endpoints and VNet’s subnets are connected. However, close the existing connects during the switch and there shouldn’t be any service endpoints be opened or closed. On turning on the Service Endpoints, Subnet applies on all the VMs and a call commits when service endpoints subsequently apply to all VM Subnet. To commit a call, it’s necessary to apply service endpoints to all VMs. You can use ACL given VNET only when the service endpoints are successfully applied. To learn more you can visit VNet Service Endpoints and rules for Azure SQL Database.






Leave A Comment