In this blog post we will explain how to leverage Azure Backup and Azure Firewall to ensure ultimate protection for your data. Azure Backup and Azure Firewall complement each other well to provide complete protection to resources and data in Azure. With the general availability of Azure Firewall Microsoft now provides a fully stateful firewall as a service that allows cloud scalability and high availability. It is designed to centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks.
Backup of Azure Virtual Machines
It is common to run Azure VMs with business-critical workloads behind a firewall. While this has proved to be an effective means to mitigate network threats one would also want to protect data in VM with Azure VM Backup. Such an extra layer of protection allows to further reduce exposure to several risks. The data in VMs is protected by safely storing it in the Recovery Services Vault. This procedure requires a network while moving the VM storage to the vault. All of the communication is performed over the Azure secure network and hence the backups will work under Azure Firewall without any actions from the user end.
It is, however, worth noting that other security measures such as NSGs, for example, can lock a VM down under network restrictions. Hence, backup of Azure VMs will work seamlessly irrespective of network restrictions applied at your end to help keep your data within selected networks and without having to perform any additional actions.
Backup of SQL Server running inside an Azure VM (in preview)
A backup extension to communicate with the Azure Backup service in order to upload backup and emit monitoring information is necessary for SQL Servers running inside an Azure VM. This extension is located within the VM and requires network access. When backing up SQL Servers running inside Azure VMs, one would need to permit the Azure Backup service to access the workload. This procedure is designed to make sure the data is restricted to Azure Backup and maintains the desired level of security.
Configure permissions for Azure Backup service to access the workload:
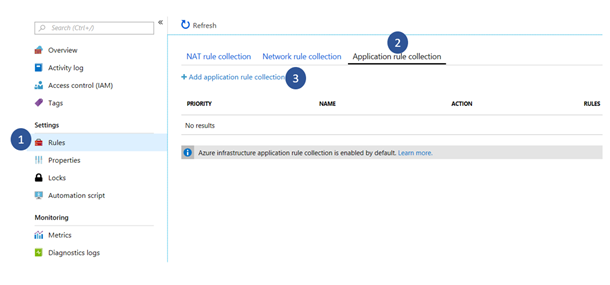
1. Inside your Azure Firewall settings go to Rules and select the Application rule collection tab. Here one can create application rules collection and edit existing collections.
2. Create a rule in an existing or new Application Rule Collection, under the FQDN tags section.
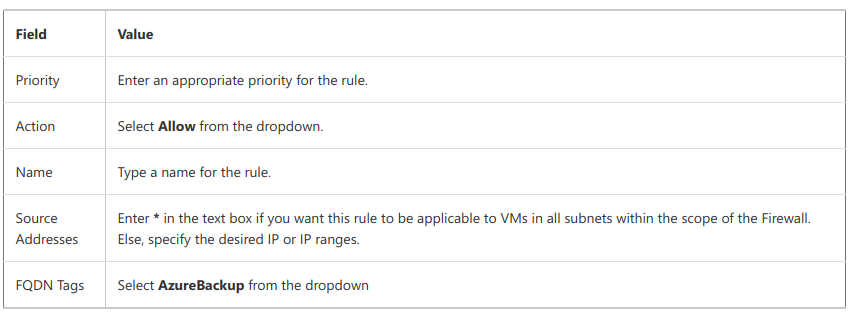
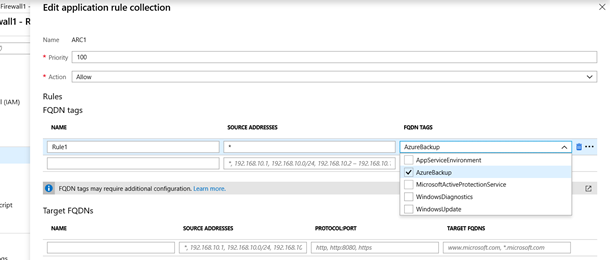
3. Select Add to create the rule. Here is a sample rule that allows Azure Backup to protect SQL Servers in Azure VMs:
Now you can back up databases inside the Azure Virtual Machine protected by Azure Firewall from any external threats.
Further reading
- Azure Backup for SQL Server on Azure now in public preview
- backing up SQL servers inside Azure Virtual Machines
- Backing up Azure Virtual Machines







Leave A Comment